ChargeLogic is now Versapay
PROCESS PAYMENTS DIRECTLY IN BUSINESS CENTRAL
Formerly a subsidiary of Solupay, which merged with Versapay in 2020, Chargelogic is now Versapay. You can access all of ChargeLogic’s payment processing capabilities, plus a variety of AR automation solutions, through Versapay, a leader in integrated payments.

Streamline payment acceptance with integrated payments

Reduce manual processes by up to 50%
Capturing and storing settlement data within an embedded payments solution lets you perform payment reconciliation in real time, saving the effort of tracking down files and manually matching payments with bank statements.
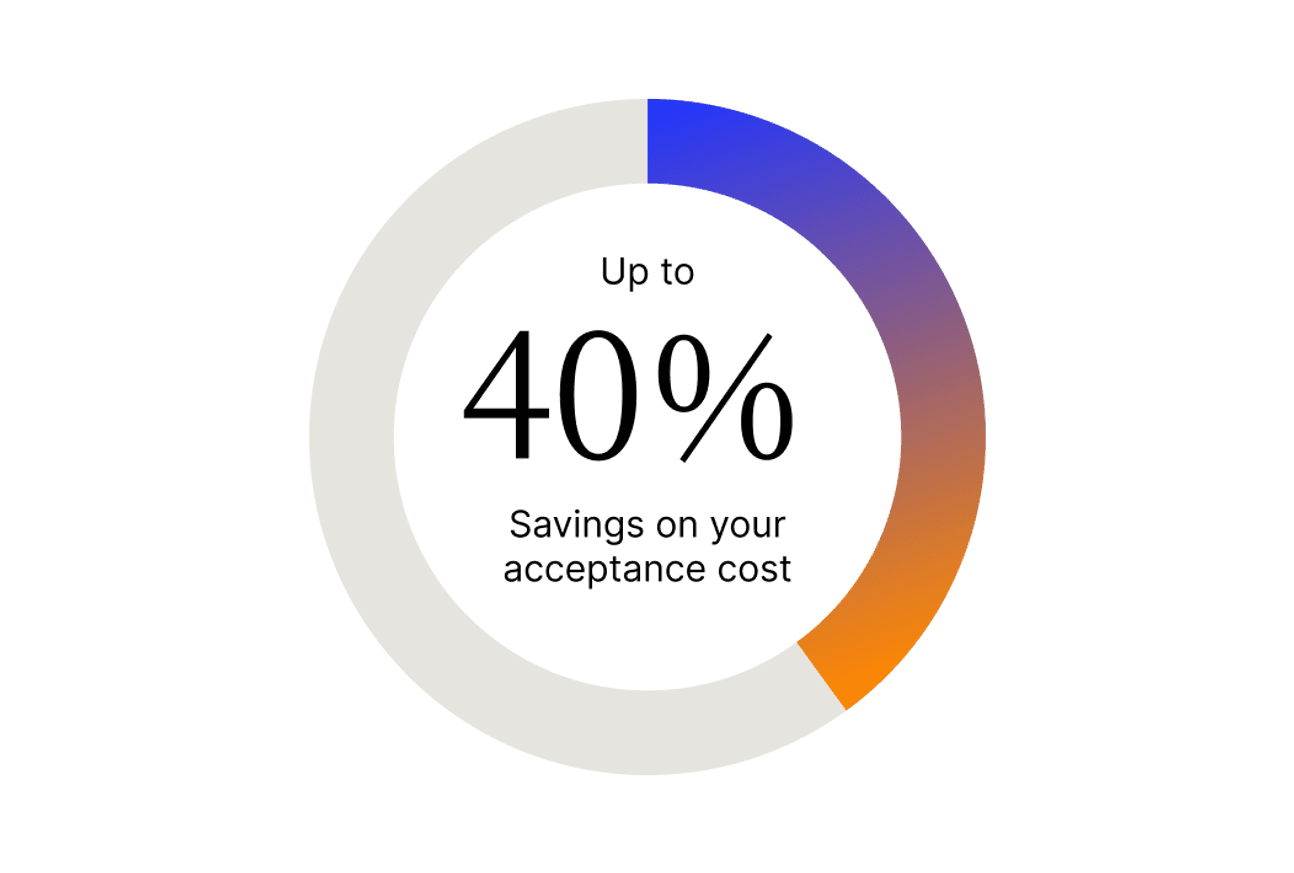
Save up to 40% on payment costs
Our integrated payment solution is designed to minimize your costs on a per-transactions basis by sending along more customer data with each transaction.

Protect against payment fraud
We use a proprietary gateway, integrate with popular shopping carts, and offer competitive merchant services. Plus, we’re PCI DSS compliant, and encrypt and tokenize credit card data.
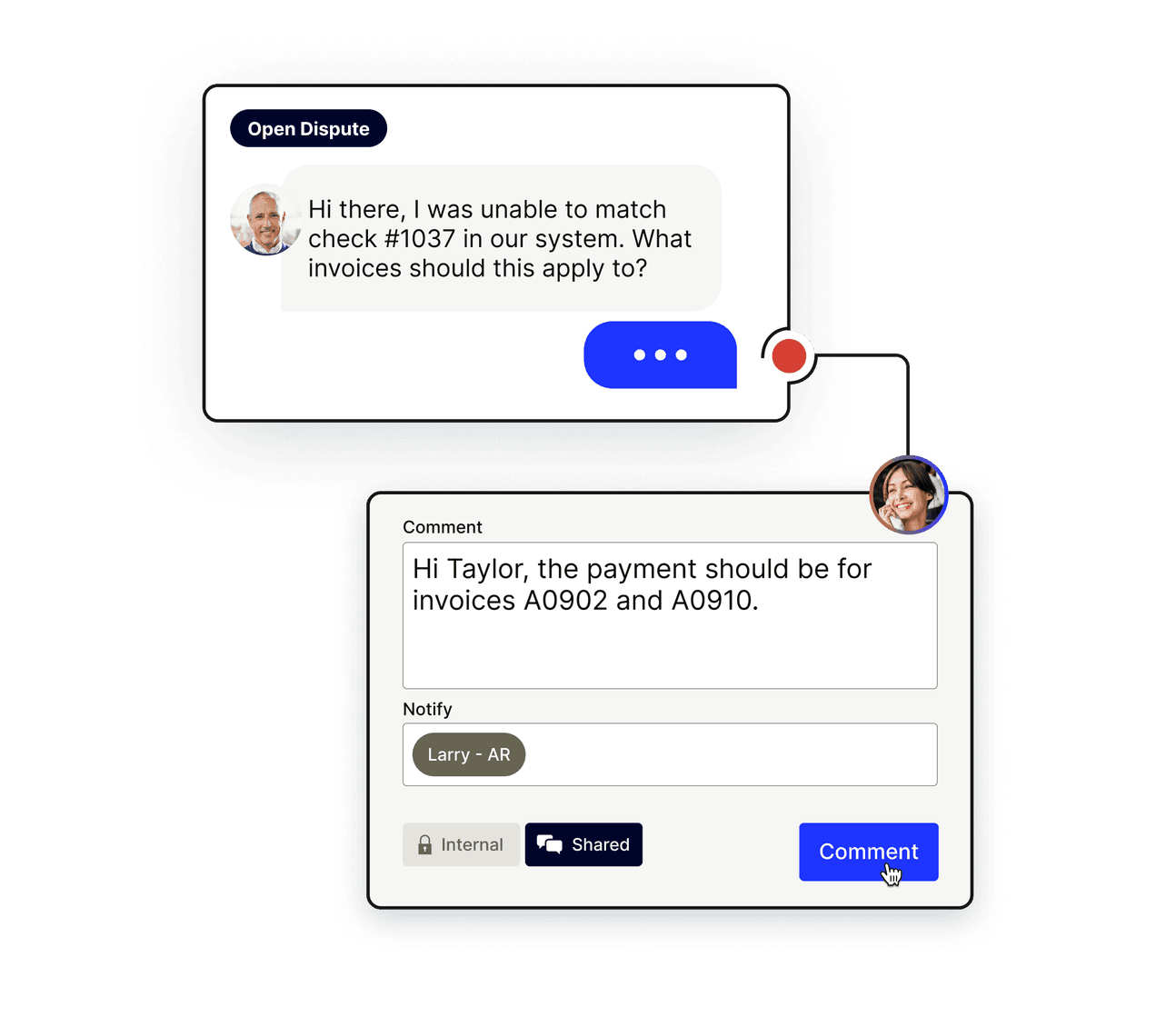
Create better customer experiences (and happier teams)
A simplified digital payment experience makes it easier for customers to track balances and resolve disputes, so they get everything they need while your AR team spends less time on tedious tasks.

70% fewer accounts 90+ days overdue
Case Study
"Using the software makes my job so much easier. It frees me up so I can learn more about the strategic part of management accounting.”
Tammy Craft, Credit & Collections Management Specialist | RPC
With Versapay, integrated payments are just the start
Our Collaborative AR Network is what you get when you take our industry-leading AR automation, give it all the collaboration tools we’ve come to expect from modern, cloud-based apps, and then add a next-generation B2B payments network.
It connects buyers and suppliers over the cloud, creating greater AR efficiencies, accelerating cash flow, and drastically improving the customer experience.

Looking for ChargeLogic support?
You can continue to access support by submitting a ticket through the ChargeLogic request form. You can also reach out to your Partner manager for information on our VersaPartner Hub.

Being a VersaPartner pays off
BECOME A PART OF SOMETHING BIGGER
If you’re an existing VersaPartner with questions, please reach out to us at [email protected].
Interested in becoming a VersaPartner? We’ll show you all the reasons why you should.